
2023 OWASP API Security Top 10 Best Practices
After four long years since the original guidelines were created, the Open Web Application Security Project (OWASP) has now updated their Top 10…
{ "term_id": 294, "name": "Stas Neyman", "slug": "stas-neyman", "term_group": 0, "term_taxonomy_id": 294, "taxonomy": "wpx-authors", "description": "", "parent": 0, "count": 8, "filter": "raw" }
The Noname Security 3.28 release supports policies to restrict API access based on IP addresses, a new method to discover and identify GraphQL APIs, and enhancements to Active Testing role-based access control.
Noname Security supports the creation of incident policies that trigger when Noname detects API traffic anomalies. With this release, you can now create a custom incident policy to track and restrict access to specific APIs from unauthorized IP addresses. Organizations can define an allowed list of IP addresses and create incidents whenever an incoming call is placed outside the allowed range. This allows companies with limited control over an API authentication mechanism to protect access to their data.
For example, a company partnering with 3rd-party services can create a policy to identify when an API call is placed outside the partner’s IP range, which may signify an attack or undisclosed data processing relationships by the partner.
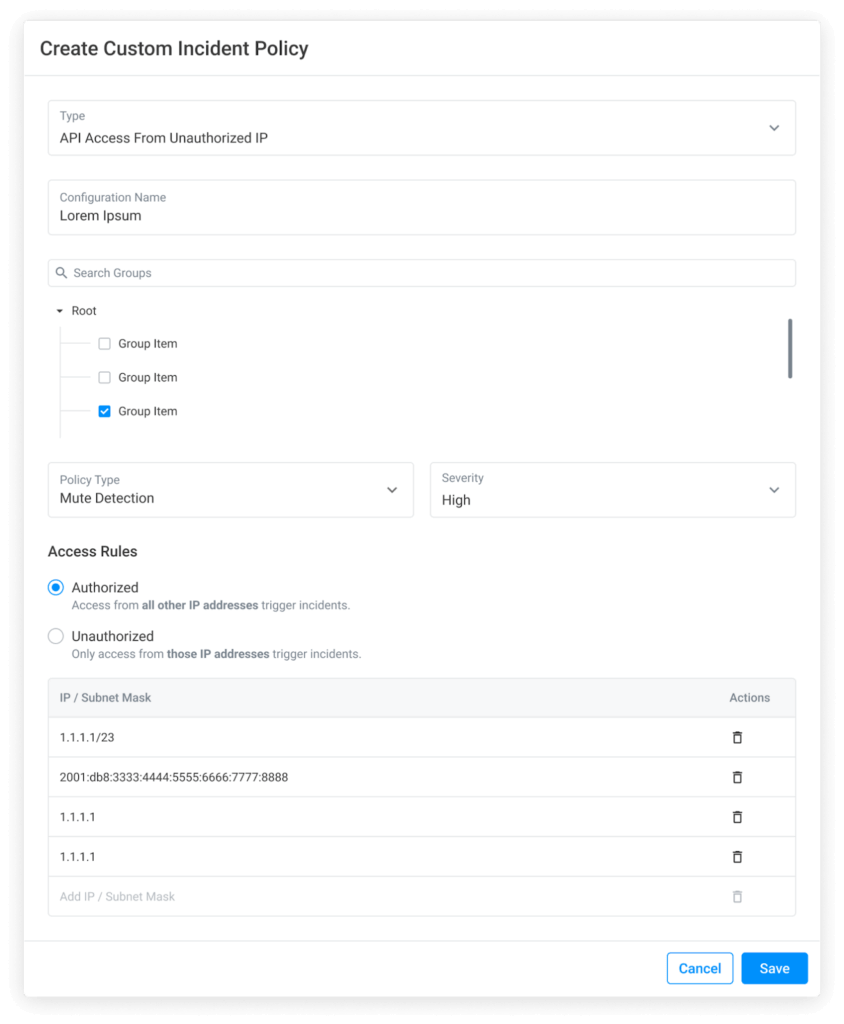
To learn more about incident policies, please see documentation.
With this release, the Noname Security platform utilizes a new method to distinguish GraphQL APIs. Previously, GraphQL APIs were distinguished based on the client-side operation name. Now, each GraphQL API is uniquely identified by a combination of the GraphQL endpoint, the type of GraphQL operation, and the top-level field. Since the top-level field represents the actual affected resource, and the operation name represents the user’s name for the specific API call, this method allows for a more precise and detailed analysis of API activities. In addition, GraphQL APIs are now presented in the GraphQL request format schema, making it easier to understand the API structure and purpose. This new approach will improve the identification of GraphQL APIs, simplify inventory management, and optimize runtime attack detection.
Active Testing supports role-based access controls (RBAC) to manage permissions within Active Testing and enforce the principle of least privilege. Previously, Active Testing roles were predefined and managed independently from the Noname Security platform. Now, all role and permission management is unified for a more seamless and streamlined experience. In addition, you can now create new roles and associated permissions to granularly control access to specific actions and areas within Active Testing.
For example, you can use roles to assign access to specific applications or application groups. This provides companies with robust access management capabilities across the entire Noname platform and simplifies permission management at scale.
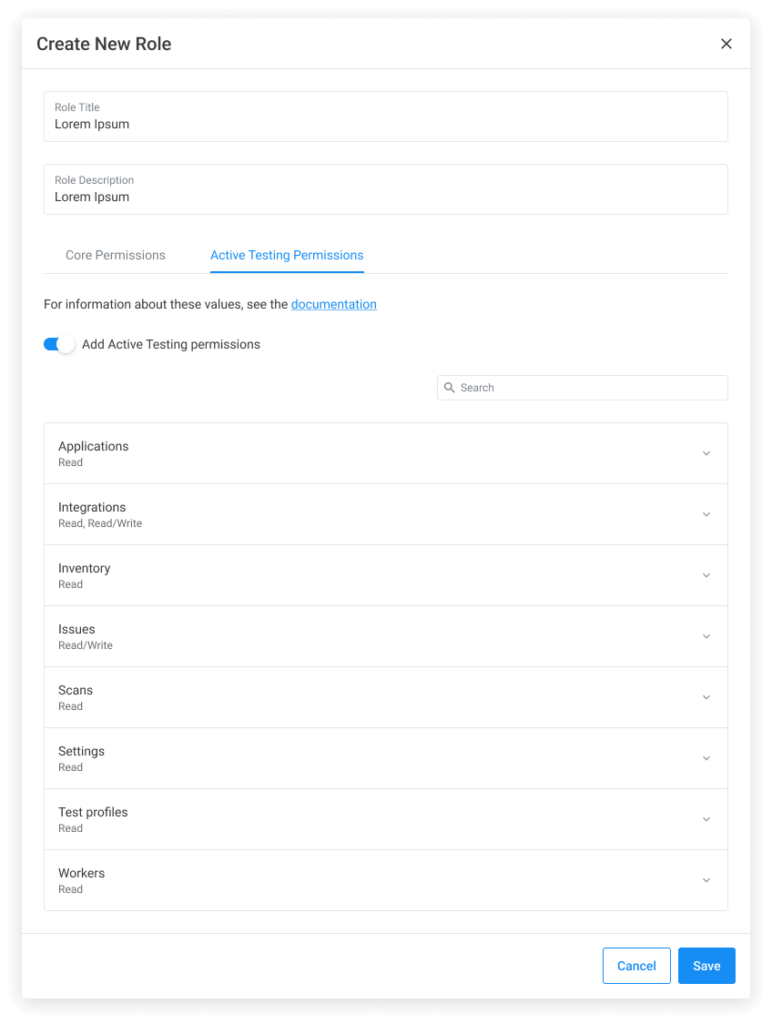
To learn more about role-based access control, please see Active Testing documentation.
For additional information about the Noname Security 3.28 release, please review the release notes.