
2023 OWASP API Security Top 10 Best Practices
After four long years since the original guidelines were created, the Open Web Application Security Project (OWASP) has now updated their Top 10…
{ "term_id": 165, "name": "Ryan B", "slug": "ryan-b", "term_group": 0, "term_taxonomy_id": 165, "taxonomy": "wpx-authors", "description": "", "parent": 0, "count": 3, "filter": "raw" }
In this blog post, we’ll discuss how your organization can implement NIST CSF 2.0 across several areas. We’ll also discuss how you can gain visibility and reduce risk with the Noname API Security Platform’s machine learning and AI capabilities.
The updated NIST Cybersecurity Framework (CSF) 2.0 was published February 26, 2024. Previously, this content was also known as the “Framework for Improving Critical Infrastructure Cybersecurity.” As stated in the framework:
The NIST Cybersecurity Framework (CSF) 2.0 provides guidance to industry, government agencies, and other organizations to manage cybersecurity risks. It offers a taxonomy of high-level cybersecurity outcomes that can be used by any organization.
In summary, the updated NIST Cybersecurity Framework is organized into the following functional categories.
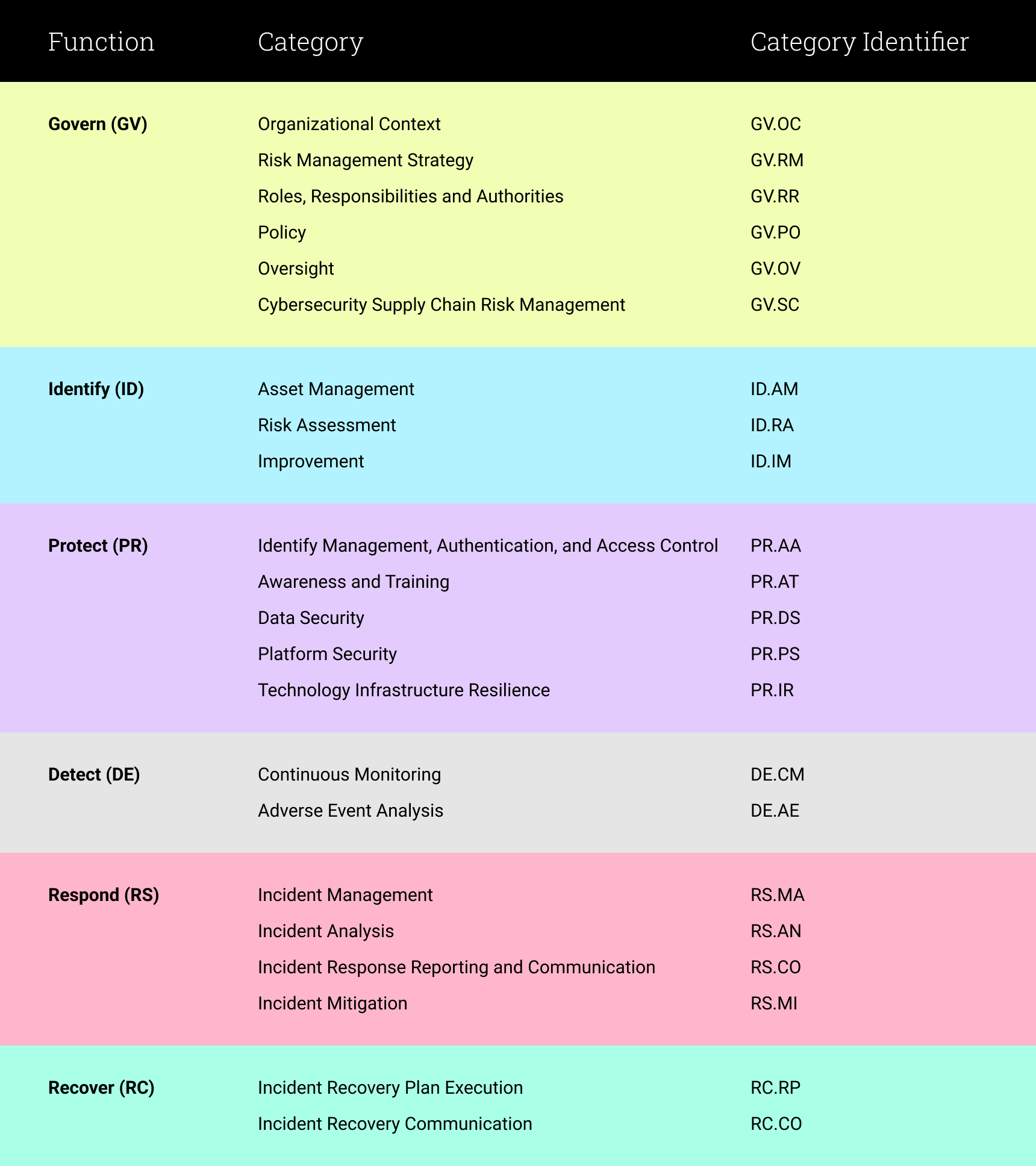
Please note:
Why focus on APIs, amid the myriad of security functions that NIST CSF 2.0 covers? Because APIs live at the core of every digital product and service today’s organizations provide to their end users, ranging from customers to citizens.
The average organization has between 15,000 and 25,000 APIs, all designed to facilitate a non-stop exchange of data. Exposed or misconfigured APIs are prevalent, easy to compromise, and often unprotected, unseen, and unmanaged. And just one compromised API can result in millions of records being stolen.
We suggest that an organization wishing to achieve a repeatable or an adaptive level of maturity should leverage a machine learning powered technology refresh approach towards implementing the NIST CSF.
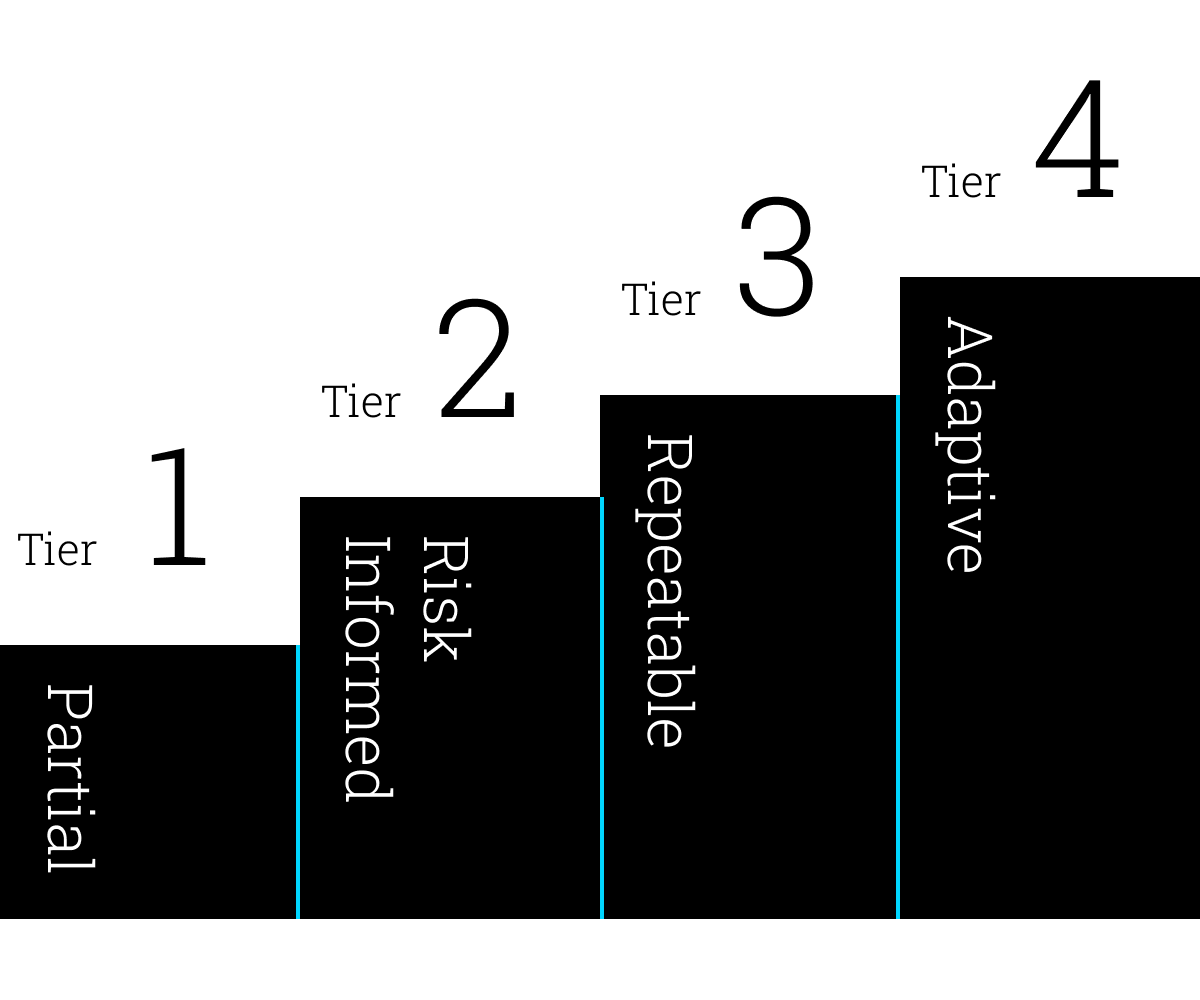
What capabilities does an organization need to reach these levels of maturity? We recommend a portfolio of machine learning-powered, AI-augmented API Security solutions that are designed to help organizations be risk-informed about infrastructure misconfigurations with:
By leveraging machine learning innovations from Noname Security in concert with the existing investments made in cloud and on-premises environments, organizations can better detect possible cybersecurity attacks and compromises.
In the following sections, we’ll explore key NIST CSF 2.0 subcategories that your team should know about. In each one, we’ll provide a brief description of the general controls needed, as well as specific examples of how your organization can strengthen its degree of visibility and protection.
Continuous Monitoring (DE.CM): Assets are monitored to find anomalies, indicators of compromise, and other potentially adverse events.
| Subcategory | Description | Example |
| DE.CM-01 | Networks and network services are monitored to find potentially adverse events. |
|
| DE.CM-03 | The physical environment is monitored to find potentially adverse events. |
|
| DE.CM-06 | External service provider activities and services are monitored to find potentially adverse events. |
|
| DE.CM-09 | Computing hardware and software, runtime environments, and their data are monitored to find potentially adverse events. |
|
Adverse Event Analysis (DE.AE): Anomalies, indicators of compromise, and other potentially adverse events are analyzed to characterize the events and detect cybersecurity incidents.
| Subcategory | Description | Example |
| DE.AE-02 | Potentially adverse events are analyzed to better understand associated activities |
|
| DE.AE-03 | Information is correlated from multiple sources. |
|
| DE.AE-04 | The estimated impact and scope of adverse events are understood. |
|
| DE.AE-06 | Information on adverse events is provided to authorized staff and tools. |
|
| DE.AE-07 | Cyber threat intelligence and other contextual information are integrated into the analysis. |
|
| DE.AE-08 | Incidents are declared when adverse events meet the defined incident criteria. |
|
Asset Management (ID.AM): Assets (e.g., data, hardware, software, systems, facilities, services, people) that enable the organization to achieve business purposes are identified and managed consistent with their relative importance to organizational objectives and the organization’s risk strategy.
Noname Security also provides awareness of cloud infrastructure ID.AM Identify Asset Management with integrations to a configuration management database (CMDB) systems inventory, making it possible for DevSecOps teams and CISO organizations to more efficiently perform their duties to provide the necessary PR.PS Platform Security and the PR.IR Technology Infrastructure Resiliency required by the business for the use case.
To properly respond and recover from a security breach or zero day vulnerability, Noname Security offers automated blocking to prevent vulnerabilities from being exploited by malicious bots or hackers and actionable integrations with DevOps and Developer work queue systems such as JIRA and ServiceNow.
RESPOND (RS): Actions regarding a detected cybersecurity incident are taken.
RECOVER (RC): Assets and operations affected by a cybersecurity incident are restored.
Incident Management (RS.MA): Responses to detected cybersecurity incidents are managed
| Subcategory | Description | Example |
| RS.MA-01 | The incident response plan is executed in coordination with relevant third parties once an incident is declared. | Detection technologies automatically report confirmed incidents. |
| RS.MA-02 | Incident reports are triaged and validated. | Preliminarily review incident reports to confirm that they are cybersecurity-related and necessitate incident response activities. |
| RS.MA-03 | Incidents are categorized and prioritized. | Prioritize incidents based on their scope, likely impact, and time-critical nature. Review and categorize incidents based on the type of incident (e.g., data breach, ransomware, DDoS, account compromise). |
| RS.MA-04 | Incidents are escalated or elevated as needed. | Coordinate incident escalation or elevation with designated internal and external stakeholders. |
| RS.MA-05 | The criteria for initiating incident recovery are applied. | Apply incident recovery criteria to known and assumed characteristics of the incident to determine whether incident recovery processes should be initiated. |
Incident Analysis (RS.AN): Investigations are conducted to ensure effective response and support forensics and recovery activities.
| Subcategory | Description | Example |
| RS.AN-03 | Analysis is performed to establish what has taken place during an incident and the root cause of the incident. | Determine the sequence of events that occurred during the incident and which assets and resources were involved in each event. |
| RS.AN-06 | Actions performed during an investigation are recorded, and the records’ integrity and provenance are preserved. | Require each incident responder and others (e.g., system administrators, cybersecurity engineers) who perform incident response tasks to record their actions and make the record immutable |
| RS.AN-07 | Incident data and metadata are collected, and their integrity and provenance are preserved. | Collect, preserve, and safeguard the integrity of all pertinent incident data and metadata (e.g., data source, date/time of collection) based on evidence preservation and chain-of-custody procedures. |
| RS.AN-08 | An incident’s magnitude is estimated and validated. | Automatically run tools on targets to look for indicators of compromise and evidence of persistence. |
Incident Response Reporting and Communication (RS.CO): Response activities are coordinated with internal and external stakeholders as required by laws, regulations, or policies.
| Subcategory | Description | Example |
| RS.CO-02 | Analysis is performed to establish what has taken place during an incident and the root cause of the incident. | Follow the organization’s breach notification procedures after discovering a data breach incident, including notifying affected customers. |
| RS.CO-03 | Actions performed during an investigation are recorded, and the records’ integrity and provenance are preserved. | Securely share information consistent with response plans and information sharing agreements. |
Incident Mitigation (RS.MI): Activities are performed to prevent expansion of an event and mitigate its effects.
| Subcategory | Description | Example |
| RS.MI-01 | Incidents are contained. | Cybersecurity technologies (e.g., antivirus software) and cybersecurity features of other technologies (e.g., operating systems, network infrastructure devices) automatically perform containment actions. |
| RS.MI-02 | Incidents are eradicated. | Cybersecurity technologies and cybersecurity features of other technologies (e.g., operating systems, network infrastructure devices) automatically perform eradication actions. |
RECOVER (RC): Assets and operations affected by a cybersecurity incident are restored.
Incident Recovery Plan Execution (RC.RP): Restoration activities are performed to ensure operational availability of systems and services affected by cybersecurity incidents.
| Subcategory | Description | Example |
| RC.RP-01 | The recovery portion of the incident response plan is executed once initiated from the incident response process. | Begin recovery procedures during or after incident response processes. |
| RC.RP-02 | Recovery actions are selected, scoped, prioritized, and performed. | Select recovery actions based on the criteria defined in the incident response plan and available resources. |
| RC.RP-03 | The integrity of backups and other restoration assets is verified before using them for restoration. | Check restoration assets for indicators of compromise, file corruption, and other integrity issues before use. |
| RC.RP-04 | Critical mission functions and cybersecurity risk management are considered to establish post-incident operational norms. |
|
| RC.RP-05 | The integrity of restored assets is verified, systems and services are restored, and normal operating status is confirmed. | Check restored assets for indicators of compromise and remediation of root causes of the incident before production use. |
| RC.RP-06 | The end of incident recovery is declared based on criteria, and incident-related documentation is completed. | Prepare an after-action report that documents the incident itself, the response and recovery actions taken, and lessons learnedDeclare the end of incident recovery once the criteria are met. |
Incident Recovery Communication (RC.CO): Restoration activities are coordinated with internal and external parties
| Subcategory | Description | Example |
| RC.CO-03 | Recovery activities and progress in restoring operational capabilities are communicated to designated internal and external stakeholders. | Securely share recovery information, including restoration progress, consistent with response plans and information sharing agreements. |
| RC.CO-04 | Public updates on incident recovery are shared using approved methods and messaging. | Follow the organization’s breach notification procedures for recovering from a data breach incident. |
In today’s threat landscape, it’s essential to understand the key requirements of global frameworks such as NIST CSF version 2.0. In addition to updating its core guidance, NIST has also introduced a suite of resources to assist organizations like yours in achieving their cybersecurity goals.
Are you seeking to learn more about API-related risks and what it takes to reduce them?
With 92% of enterprises having experienced an API security incident, organizations also need guidance on the vulnerabilities and attack methods that are central to protecting APIs. Industry experts turn to the “2023 API Security Top Ten,” a report from the highly respected non-profit Open Web Application Security Project (OWASP).
You can learn about the OWASP Top Ten – and best practices for preventing API breaches – in a convenient eBook we published to help security teams.