
Definitive Guide to API Discovery
Shadow and rogue APIs operating freely are putting your organization at risk.
{ "term_id": 161, "name": "Filip Verloy", "slug": "filip-verloy", "term_group": 0, "term_taxonomy_id": 161, "taxonomy": "wpx-authors", "description": "", "parent": 0, "count": 14, "filter": "raw" }
The parable of the blind men and an elephant is a story of a group of blind men who have never encountered an elephant before, and who learn and imagine what the elephant is like by touching it. Each blind man feels a different part of the elephant’s body, but only one part, such as the side or the tusk. They then describe the elephant based on their limited experience, and their descriptions of the elephant are different. The moral of the parable is that humans tend to claim absolute truth based on their limited, subjective experience, as they ignore other people’s limited, subjective experiences, which may be equally true.
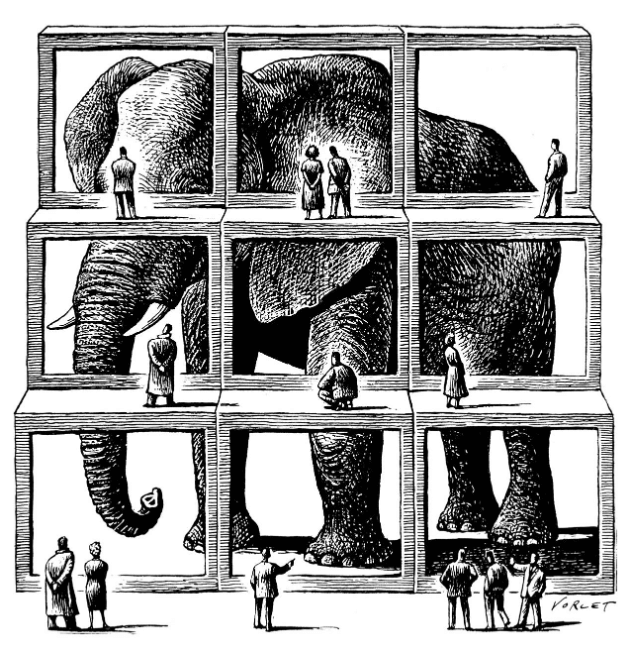
The same is true for existing security controls and new attack vectors they have never encountered before. Take for example the Web Application Firewall, or WAF, which is extremely competent in dealing with HTTP transaction based security using signature based detections. Over time, the application landscape changed and most traffic became API based (according to Akamai, up to 83% of the traffic is API based) But inline tools, like the WAF, did not adopt. They were left essentially blind to this change and still assumed the traffic was HTTP based, which it mostly is for APIs, making this even more complex.
Different API types, like RESTful API, leverage HTTP methods to communicate and exchange data. You would be forgiven to lean on your existing WAF to try and manage this.
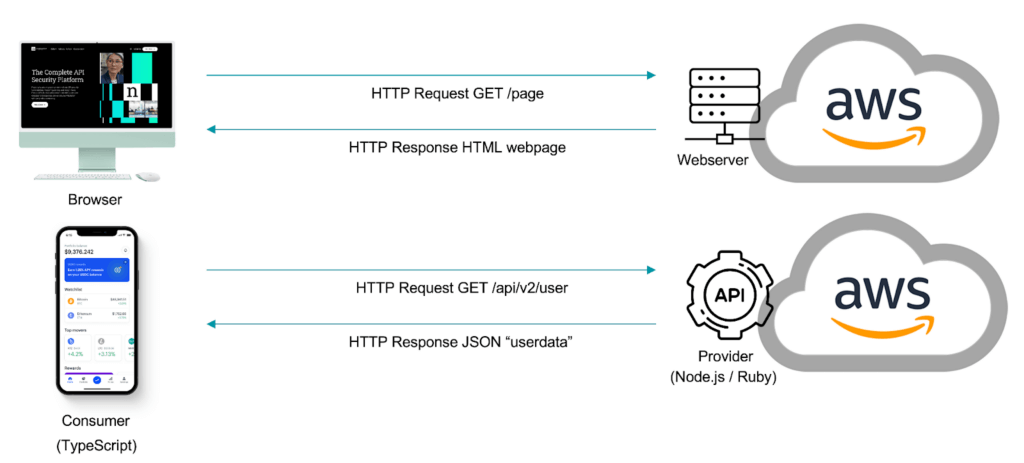
From a security perspective, however, they are wholly different. Just like with the blind men, your inline devices miss context. They only see a small piece of the information and will jump to the wrong conclusions, in security meaning false positives or false negatives causing disruptions or providing you with a false sense of security.
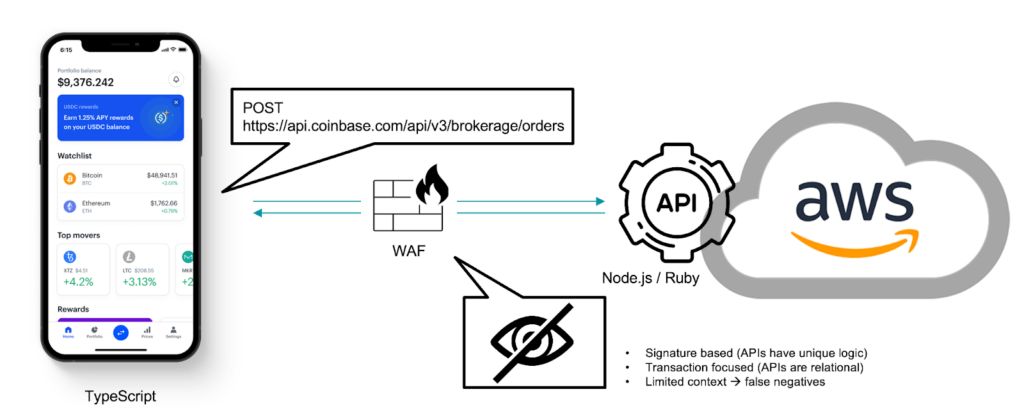
Imagine your WAF evaluating the API call below. From an HTTP rules perspective, it looks legitimate. The app and user are authenticated and authorized to talk to the API over HTTP, but the WAF cannot determine the legitimacy of the interaction with the API, i.e. if the business logic is being used in correspondence with the organization’s expectations. For example, is the user trying to skip steps in the order process, trying to clear an order before going through the payment steps, for instance.
To see the full elephant, you need to step back and see all the pieces, and understand them in context. The API security platform provides the context and all the pieces.
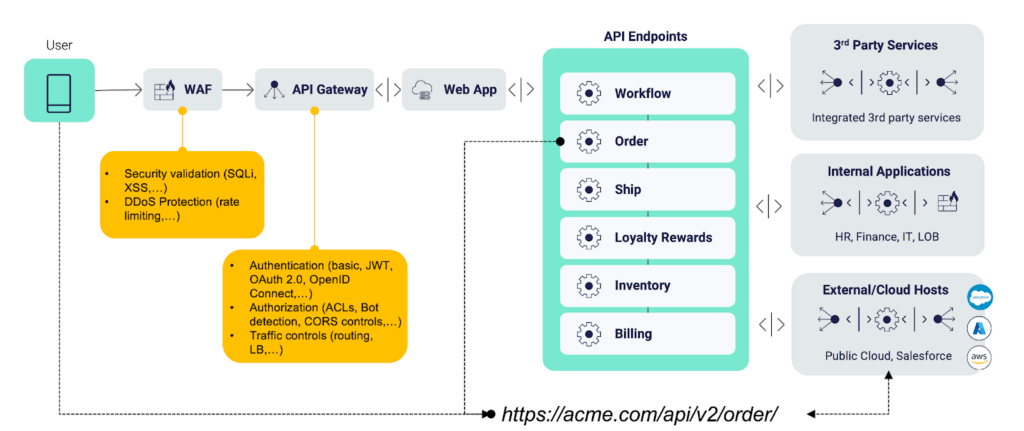
Noname Security’s API Security Platform enhances the capabilities of the WAF, or the API Gateway, by looking at the full extent of the API transactions over time and linking them to individual users, thereby enabling them to differentiate between good and malicious behavior.
The context we gather comes from our understanding of the usage and capabilities of each individual API. Once we have this baseline of expected behavior, we can validate each new interaction and look for deviations indicative of malicious behavior. Once we make that validation, we leverage your existing WAF or Gateway to block the malicious user and safeguard your digital estate.
Beyond passing through the WAF and the API Gateway an API connects together an entire ecosystem of services. Understanding how users interact with different endpoints and how the natural flow of the endpoints and their back-end functions are supposed to be consumed is the purview of the dedicated API security platform. Even application security testing would fall short here, as it does not comprehend the concept of an endpoint. In other words, not only would it not see the elephant, it would not even understand the functionality of the trunk.
Application Security Testing is ideally suited to test just that, application code, but APIs present back-end application functionality as endpoints so testing the API code itself will provide you a false sense of security. Dedicated API security testing will discover all endpoints (to give you the full picture of the elephant) and then test their security posture.
The Platform capabilities provide full API discovery, what are all the elephants you need to manage, posture management of those APIs, i.e. spotting any misconfigurations with your APIs, runtime security to detect behavioral issues, and API security testing to avoid releasing any API security vulnerabilities into production.
Now the Noname Security Platform is part of a bigger security ecosystem still, feeding our detections into systems like SIEM, SOAR, and ITSM solutions to provide the back-end teams tasked with remediation with the needed context as well.