Platform Features
By Need
By Industry
Partner Program
Our Partners
Resource Center
{ "term_id": 294, "name": "Stas Neyman", "slug": "stas-neyman", "term_group": 0, "term_taxonomy_id": 294, "taxonomy": "wpx-authors", "description": "", "parent": 0, "count": 8, "filter": "raw" }
The Noname Security 3.27 release includes capabilities to assess and visualize the risk of your API landscape, a user-friendly visual interface for creating and automating workflows, improved support for external API definition files, and more.
The API risk scoring is a new feature in the Noname Security platform that allows you to assess the risk of individual API Endpoints in your API inventory. An API’s risk score is calculated by combining the risk assessments of multiple parameters, such as the sensitivity of data accessed by an API, the number of API requests, whether the API is internal or internet-facing, and more. API risk scores can help you understand the probability and impact of a potential API Endpoint exploit and proactively implement compensating controls.
By default, Noname Security provides weights and scores for the parameters based on best practices. However, you can also customize and adjust both the weights and the scores to better reflect the nuances of your application environment and risk tolerance. For example, you can increase the weight for specific parameters that are more important for your organization or affect specific APIs. You can then focus your efforts and resources more effectively on protecting the most critical and vulnerable aspects of your digital environment.
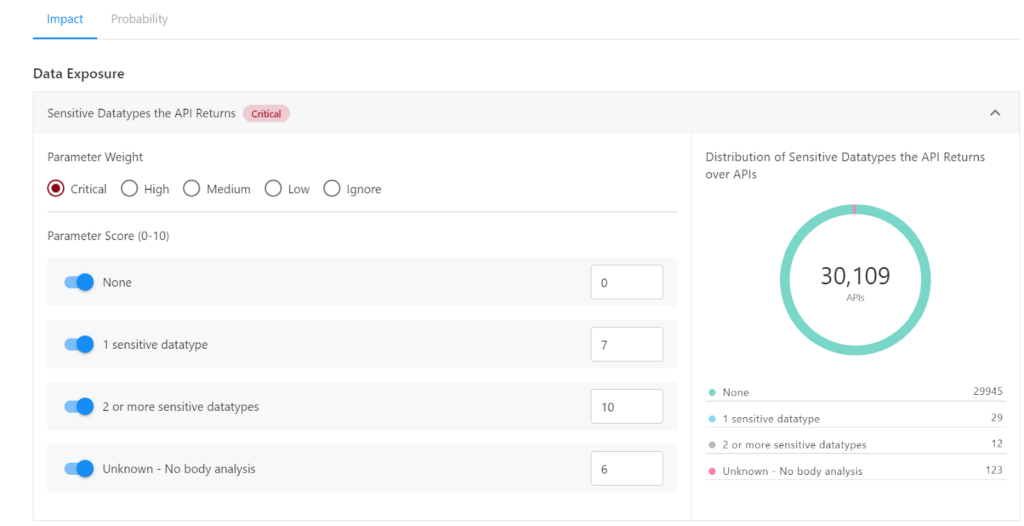
To learn more about this feature, please visit the API Risk documentation.
Workflow Automation is a new capability in the Noname Security platform that improves efficiency and productivity by simplifying the creation and management of multi-action workflows. With Workflow Automation, organizations can automate complex event response processes and synchronize incident-related data between the Noname platform and 3rd-party services, including ServiceNow, JIRA, Azure DevOps, and others.
Workflow Automation is easy to use through a user-friendly visual editor — no coding necessary — and workflows can be built in minutes leveraging customizable workflow samples and a database of over 300 pre-built connectors.
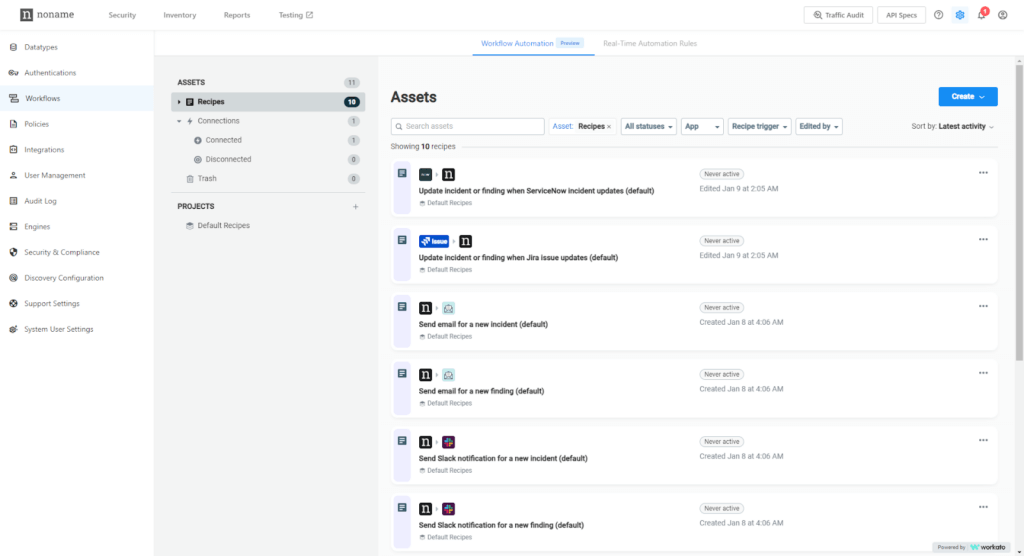
Common use cases that can be addressed using Workflow Automation include:
Workflow Automation capability is currently in Public Preview for SaaS customers. To learn more, please visit the Workflow Automation documentation.
The Incident Tracking feature is a new capability in the Noname Security platform that continuously tracks attacker activity from the moment an excessive activity is detected. Excessive data incidents can occur when attackers compromise large quantities of data from your organization. As the attack progresses, the platform dynamically updates the incident details to reflect the latest exfiltrated data and attacker actions. This ensures that security teams have access to the most current information, enabling them to make informed decisions and take appropriate actions.
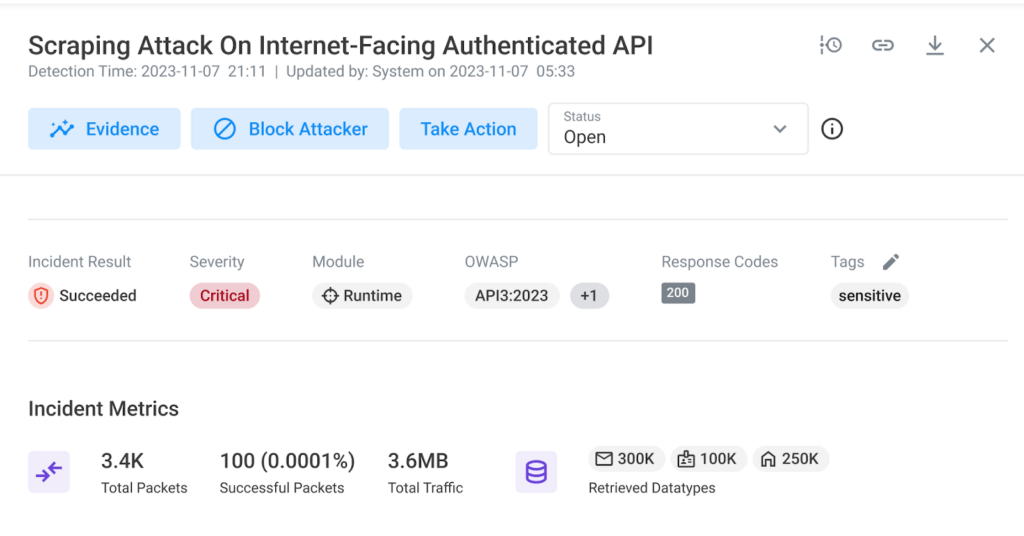
This feature enhances high-risk attack prioritization with an ‘Active’ icon indication, enabling quicker and more effective threat response.
To learn more about this feature, please visit the Incidents documentation.
An API that returns more data than necessary or intended can be a sign of excessive data exposure and indicate that an attacker is compromising sensitive data from your organization. With this release, you can now gauge the impact of an excessive data attack by reviewing the new Incident Metrics field. With Incident Metrics, you can see the total number of packets affected, the number of successful attacks, and the specific data types targeted over the previous 24 hours, offering a comprehensive overview of the incident’s impact. For example, in the event of a scraping attack targeting an API that retrieves discount coupons, you can now ascertain the exact number of coupons compromised.
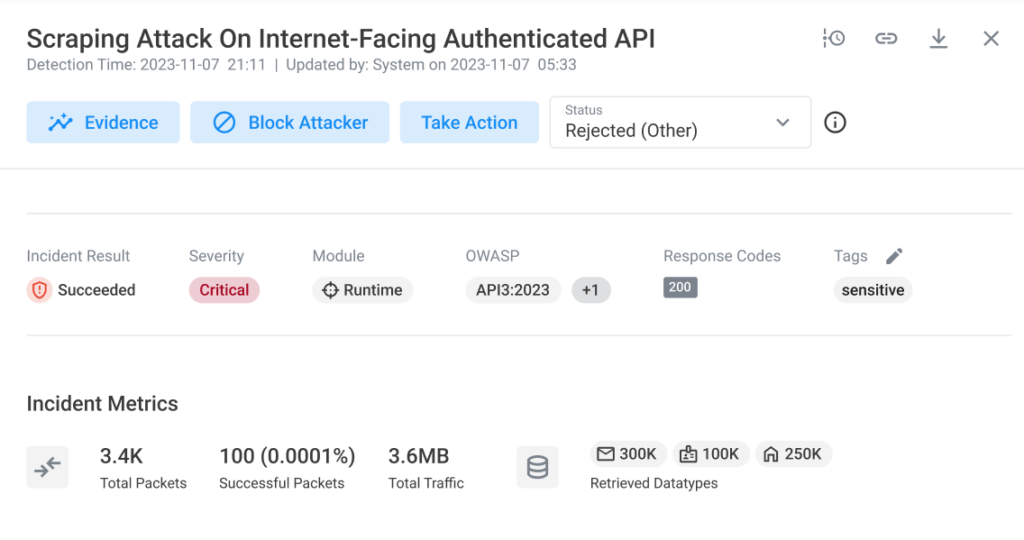
Should abnormal behavior persist or escalate beyond the initial 24-hour analysis period, the Noname platform will create a new incident, ensuring that ongoing threats are continuously prioritized and addressed.
To learn more about this feature, please visit the Managing Incidents documentation.
With this release, Noname combines traffic source and prevention integrations into a singular process. Previously, the Noname Platform’s traffic source integrations only allowed you to analyze API traffic for vulnerabilities from various environments. At the same time, the prevention integrations only enabled you to block suspicious or harmful API runtime activity. Now, traffic analysis and prevention integrations are combined into a unified plugin, eliminating the need for separate configurations for traffic ingestion and attack blocking and offering a more efficient deployment experience.
For example, the Kong prevention integration was previously treated as a distinct component. Now, it is incorporated into the Kong traffic source plugin, consolidating the configuration process and enhancing the overall functionality. Similarly, blocking capabilities have been extended to the NGINX traffic source integration.
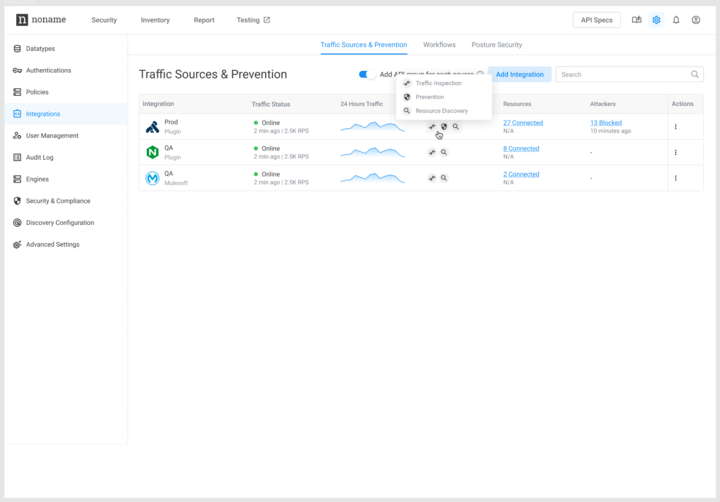
You can enable either or both features for each source integration, enhancing the platform’s adaptability to fit specific security needs and operational requirements of your deployment.
To learn more about this feature, please visit the Integrations documentation.
API headers allow companies to include contextual information about APIs, such as which application the API supports, the purpose of the API, and the application owner. With this release, you can now use the information contained in API headers to tag your APIs automatically. This eliminates the need to manually map each API to its corresponding application and reduces the overhead of finding the API owner. For example, since the Noname platform automatically tags your APIs with the correct application name and owner, you can use these tags to sort and filter your API inventory more efficiently. In addition,
the automated extraction and tagging process ensures that APIs are accurately categorized, allowing for more effective governance, security, and operational management.
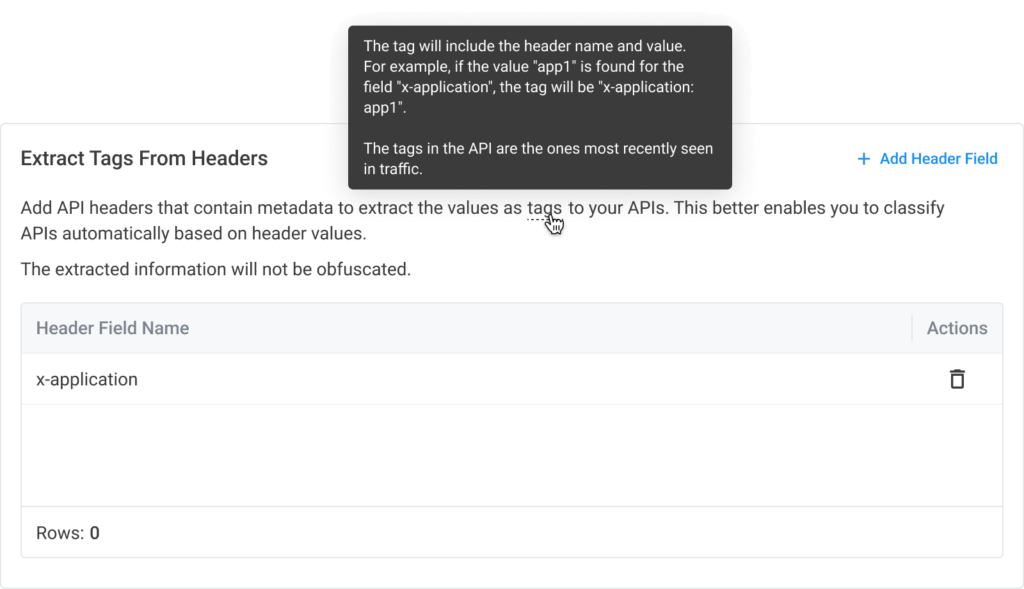
To learn more about this feature, please visit the documentation here.
API Specs are widely used for describing APIs, and many APIs already have a spec file available. The Noname platform allows you to upload API specs into the Noname platform and compare your API traffic to API Spec definition files to identify discrepancies between production and development environments. With this release, you can now edit the servers in your API specification files as part of the upload process or modify them after you upload the specs through the management API. This simplifies the comparison of APIs in your inventory to the OpenAPI specs. For example, suppose your OpenAPI definition file contains non-production servers. In that case, you can now easily update them and validate that production APIs perfectly match your API specifications.
In addition, the Noname platform now supports importing APIs from RESTful API Modeling Language (RAML) definition files. RAML is widely used in the Mulesoft environments to model and describe APIs. This allows you to add APIs to your inventory from RAML specifications without connecting any traffic source and analyze APIs for vulnerabilities.
All API spec file management, including upload, modification, and deletion, can be performed programmatically using the Noname Management API.
To learn more about this feature, please visit the documentation.
The Attacker Page is central to the Noname platform, and with this release, the page design is streamlined to create a better user experience for more efficient threat analysis. Now, the page provides more clarity and visibility into essential information and allows security teams to quickly identify and investigate incidents and attackers. For example, the strategic grouping of data points allows you to understand the context and specifics of each attack and focus on the most relevant information without being overwhelmed by excessive details.
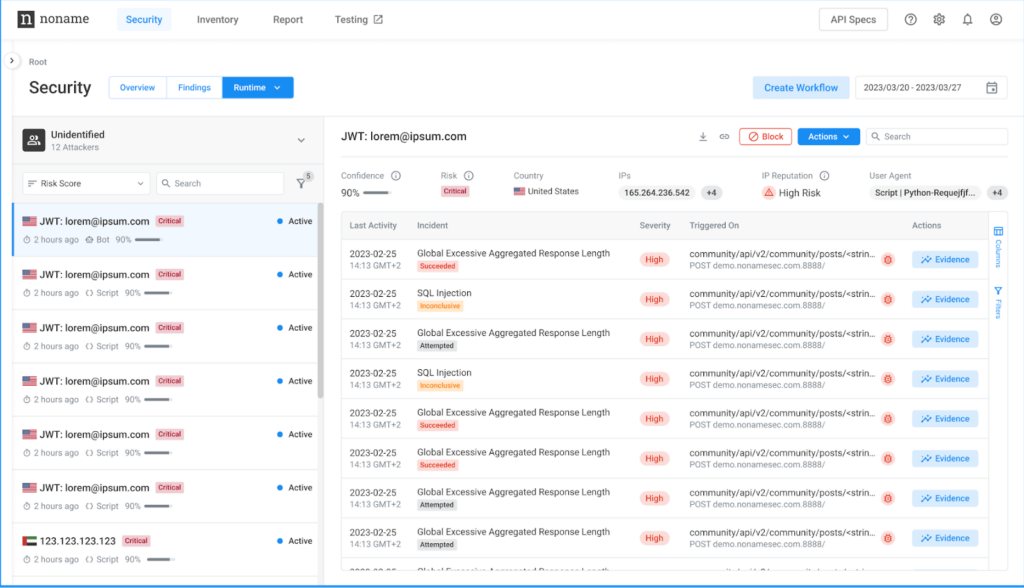
To learn more about this feature, please visit the Managing Attackers documentation.
The Global Scan Status feature centralizes the reporting of scans across all applications, enabling you to view scans currently in progress, stop, cancel, or delete scans, and access a history of the 20 most recent scans, all from a unified location. This centralized approach simplifies the scanning process and facilitates a more efficient management and review of scan results.
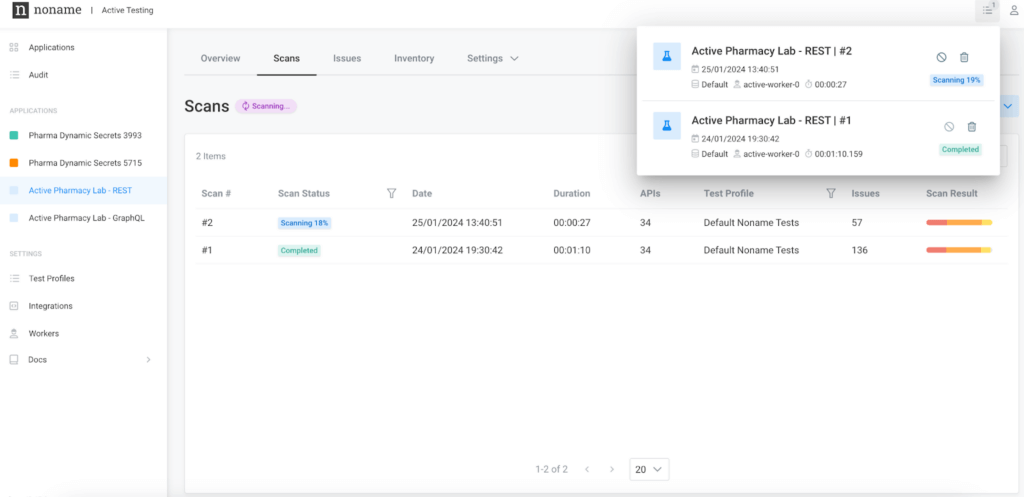
By aggregating scan status information and history in one place, you can efficiently assess the security posture across your entire application landscape.
API headers can include important metadata that ensure API requests are successful. This metadata can include information about the API, including a value string called “user agent” to identify the application, service, or user responsible for making an API request. With this release, you can now use Active Testing to add custom headers to APIs and define a custom value for the Active Testing attacker user agent. This ensures you can identify requests sent by Active Testing, and avoid applying security controls that can prevent the execution of Active Testing tests or erroneously flagging these requests as potential security threats.
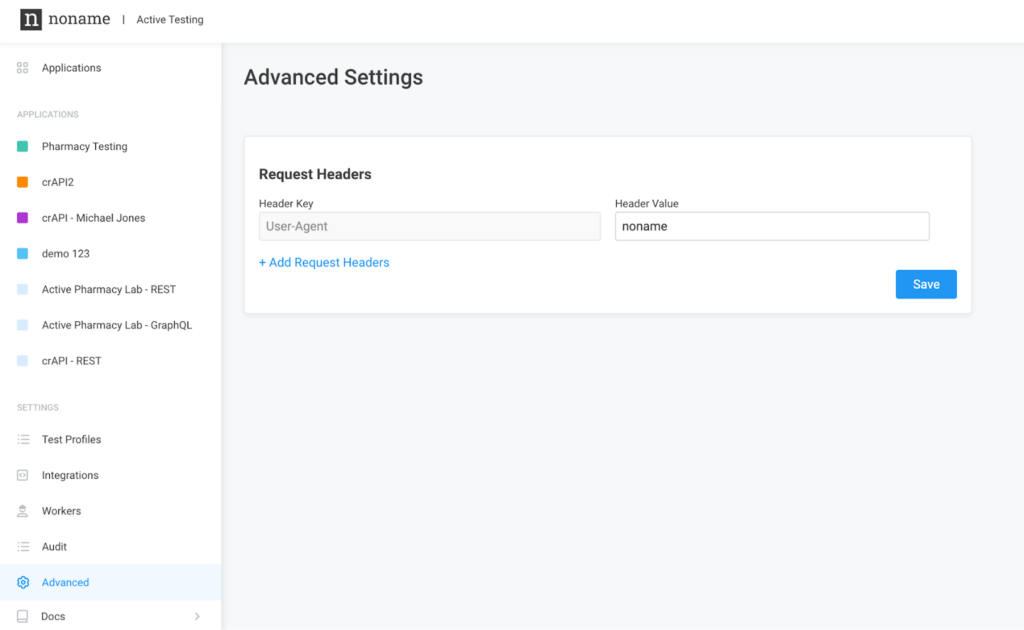
To learn more about this feature, please visit the Configuring Custom Headers documentation.
For additional information about the Noname Security 3.27 release, please review the release notes.