
API Security Testing for Dummies
Organizations now have an average of 15,000 APIs to secure, and this number is growing rapidly as thousands of new applications hit the market…
{ "term_id": 161, "name": "Filip Verloy", "slug": "filip-verloy", "term_group": 0, "term_taxonomy_id": 161, "taxonomy": "wpx-authors", "description": "", "parent": 0, "count": 14, "filter": "raw" }
Recently, we announced the general availability of Active Testing V2, our flagship API security testing solution, and an integral part of the Noname API Security Platform.
The more API security defects we can catch during development, the cheaper and more efficient our applications become. So-called shifting left has a profound effect on security if done right. Over 85% of defects, including security issues, are created in development, mainly during the initial coding phase. When testing happens at a late stage in the development process, those defects aren’t found until just before new products and updates are released. That means defects and the vulnerabilities they create get released to production, and new development begins that depends on faulty code. When those issues are finally found in production, the cost of repair skyrockets, because now the organization has to remediate the issue. This can mean refactoring code, taking systems offline, which can already be serving thousands of customers, and rolling back revenue-generating products. Of course, if a vulnerability is exploited, it can also cost millions of dollars, depending on the breach.
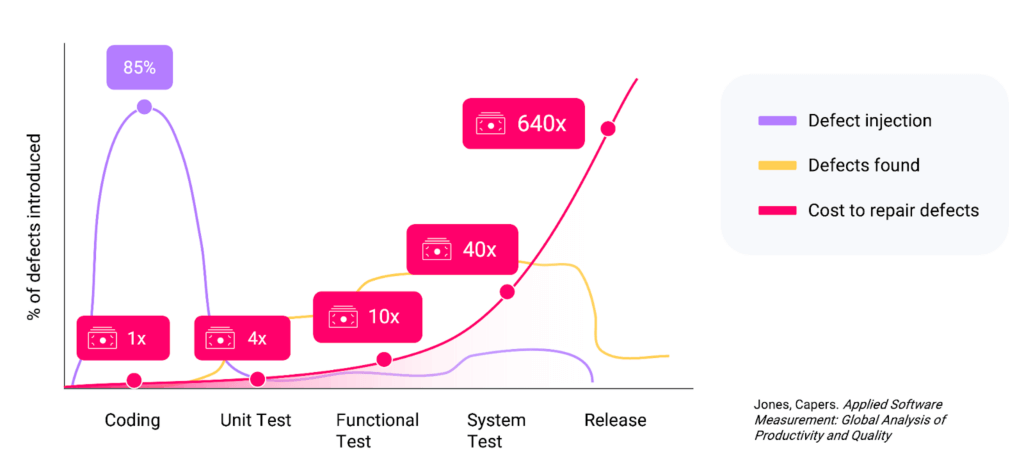
In an ideal world, we wouldn’t have vulnerable APIs and would be able to catch all API security defects before they are released into production.
With our latest Active Testing release, we are doubling down on making sure all dependencies are accounted for, leaving no API untested, increasing the confidence of our customers, and ultimately speeding up the development of new and improved services.
Active Testing V2 was built from the ground up to specifically address the challenges of testing APIs for security vulnerabilities. Noname Security Active Testing includes:
Our best-in-class reachability is key to ensuring we test all aspects of the APIs you are developing. An API can be complex, especially from a security perspective. Therefore, we need to ensure we cover all our bases. As Active Testing builds out the inventory of the API based on very minimal customer input, we ensure all pathways are covered. If some endpoints aren’t immediately reachable, and therefore untestable, we provide the tools to quickly and easily adjust the environmental settings to remedy this.
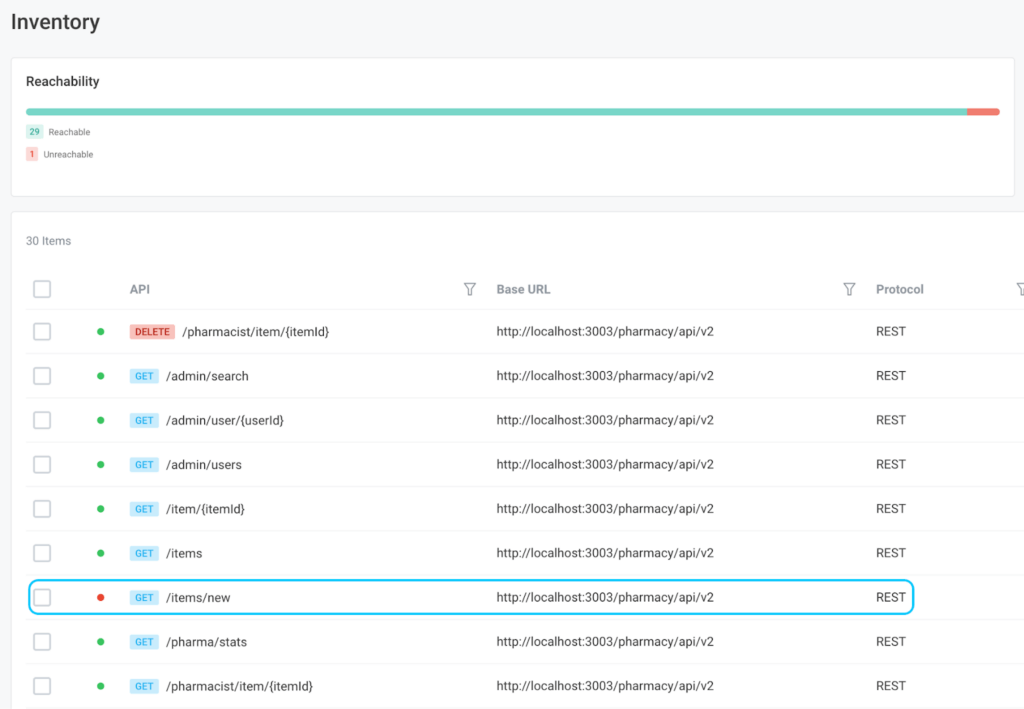
APIs are unique in that most of the advanced security vulnerabilities manipulate the business logic provided by the API. To understand the business logic, you need to understand all its individual components and dependencies. A dependency is a connection between APIs, in which one API consumes information from another API. Without understanding the dependencies, we cannot truly understand their security implications. Additionally, the API consumes and presents resources. These are considered a server-side object with which your APIs interact. Proper testing will automatically identify which resources are handled in your application, and identify how your APIs affect those resources in relation to the different API operations (CRUD).
Shifting security left, i.e., performing security testing earlier in the development process, shouldn’t increase developer toil. We need to be careful not to overwhelm our precious resources and make it a seamless part of their existing workflows. To achieve this, Active Testing natively integrates into your existing CI/CD toolchain and simply becomes an additional gate to pass on the road to success.

From a developer perspective, security testing becomes part of your DevOps fabric, and you decide the level of interaction which you feel appropriate. You have the ability to break the build pipeline in case of a severe defect, or simply be provided with informational output you can action later.
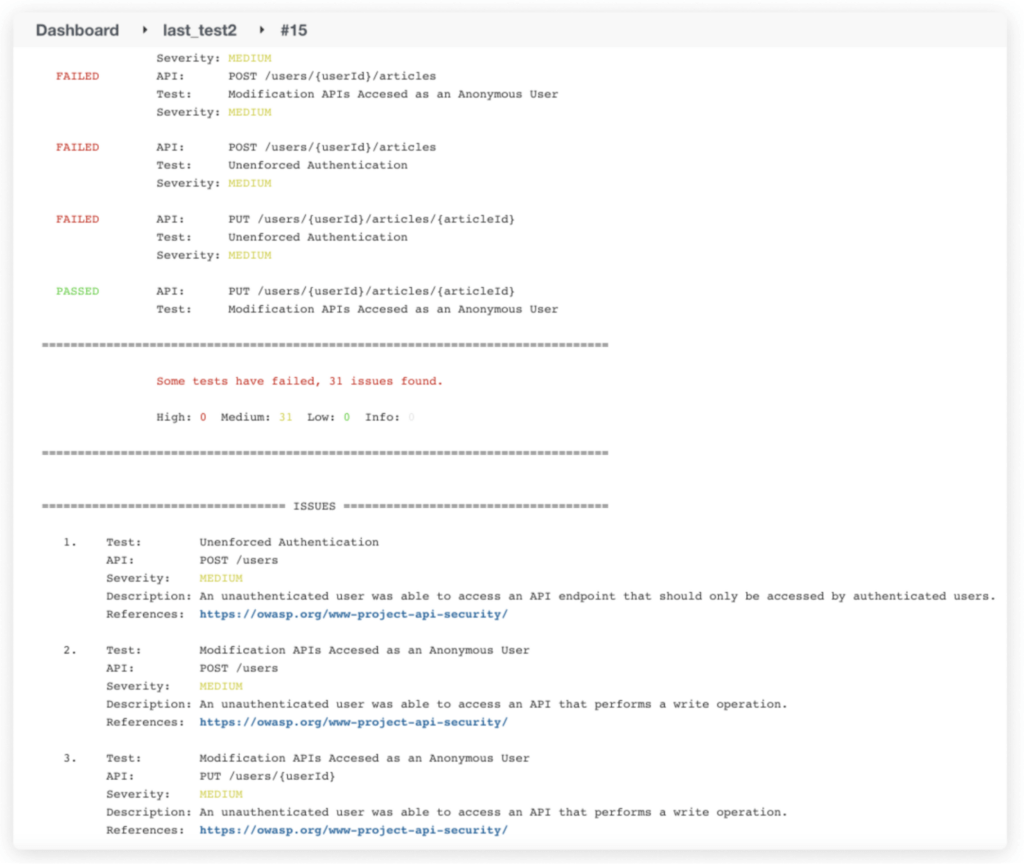
The output of our automated security testing needs to fit existing organizational processes. Therefore, we can automatically create and assign ticket based (like Jira) follow-up to the correct teams for remediation.
I’m excited to bring our next-generation API security testing capability to our customers, and continue our push for a safer digital world.
To learn more about how Active Testing can help you deliver secure APIs faster, visit nonamesecurity.com/security-testing.