Platform Features
By Need
By Industry
Partner Program
Our Partners
Resource Center
{ "term_id": 294, "name": "Stas Neyman", "slug": "stas-neyman", "term_group": 0, "term_taxonomy_id": 294, "taxonomy": "wpx-authors", "description": "", "parent": 0, "count": 11, "filter": "raw" }
The latest Noname Security 3.31 update includes API classification rules that make managing API inventory easier and more efficient. It also features several UI enhancements to simplify the end-user experience with the Noname API Security platform.
The Noname Platform now offers API classification rules to streamline filtering and categorizing API endpoints, making API inventory management easier. With this update, you can set up API classification rules to automatically label APIs with appropriate tags and owners. Previously, these tasks had to be done manually for each API or in bulk. Now, you can create rules based on specific criteria to automatically classify existing and newly added APIs. This allows for efficient management of your API inventory and quicker resolution of issues. For instance, you can create a rule to label any public-facing APIs that use basic authentication as “high-risk,” and assign an API owner based on the application name in the API header. This will enable you to review these high-risk APIs with their respective owners and decrease the chances of a potential breach.
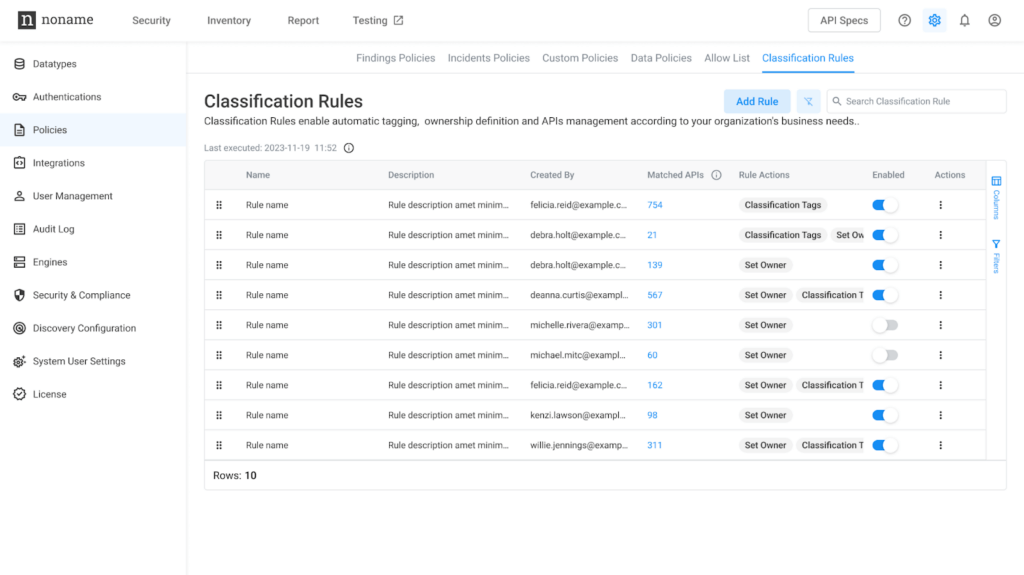
To learn more about this feature, please see the documentation for Classification Rules.
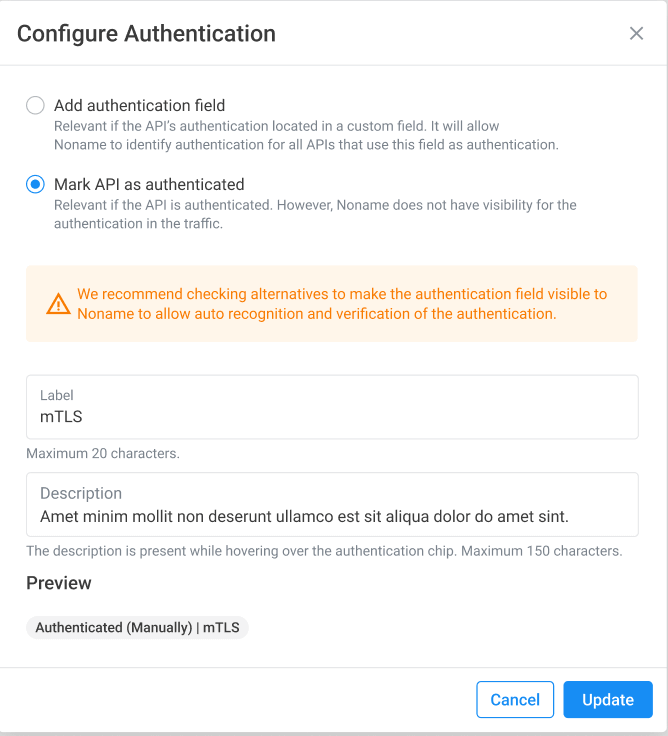
Noname Security Platform can determine whether an API is authenticated by analyzing the API traffic. However, in some cases, such as when a mutual transport layer security (mTLS) protocol is used, the authentication information cannot be extracted by observing the traffic. In these scenarios, you can now manually configure the authentication status and mark APIs as authenticated. This reduces the number of false-positive findings and improves the accuracy of your API inventory.
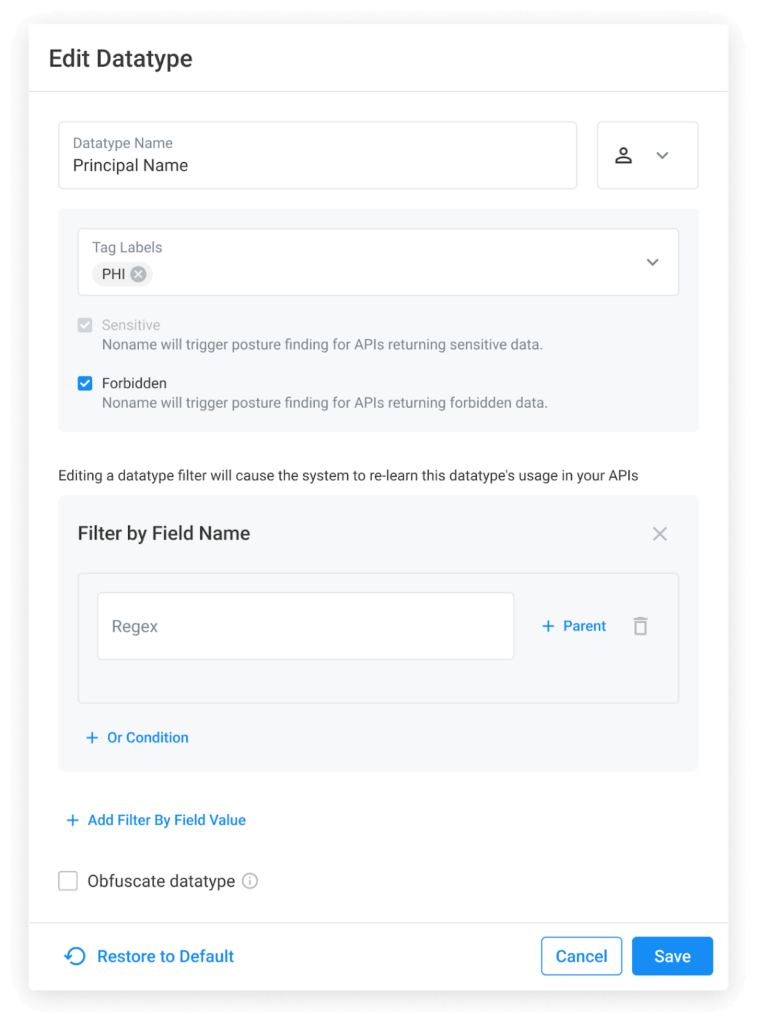
The Noname platform relies on datatype tags to effectively identify, analyze, and prioritize API incidents. This release makes it easier to choose the Forbidden and Sensitive tags when creating or modifying your datatypes. The Sensitive tag is typically used for data that is personally identifiable or restricted, such as addresses, and should not be accessible through an API without proper authentication. The Forbidden tag is used for any data that should never be shared through an API, such as passwords or other credentials. Applying the correct tags ensures that any issues related to these high-risk datatypes are promptly brought up for review and remediation.
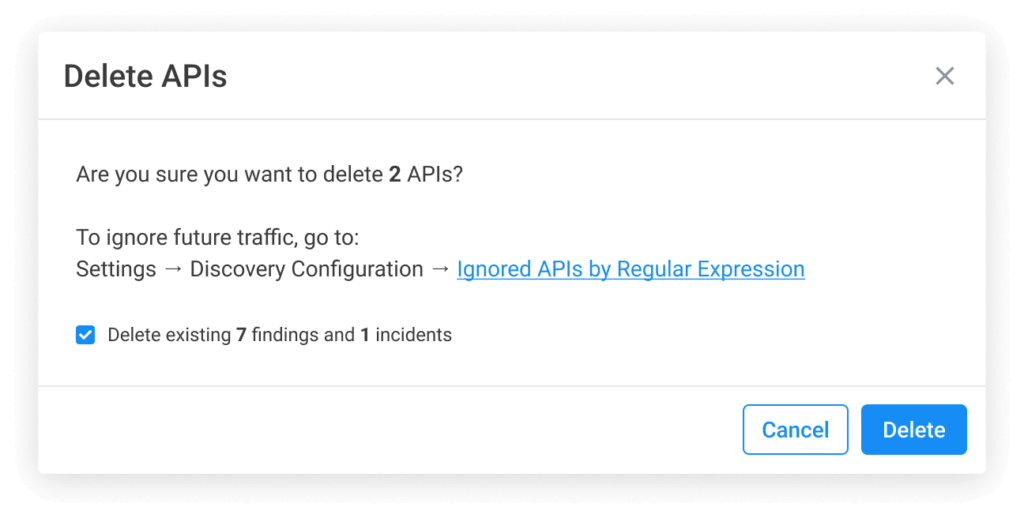
It is now possible to remove specific APIs from your inventory without altering the API discovery rules. Previously, you could set up rules for traffic analysis to disregard APIs that met certain criteria in their host, path, or method. This prevented those APIs from being included in the inventory. Now, you can delete APIs without creating these rules. For example, you can delete any APIs discovered during the implementation phase and make sure that only production APIs are included in your inventory. This gives you more flexibility in managing your API inventory and improves accuracy.
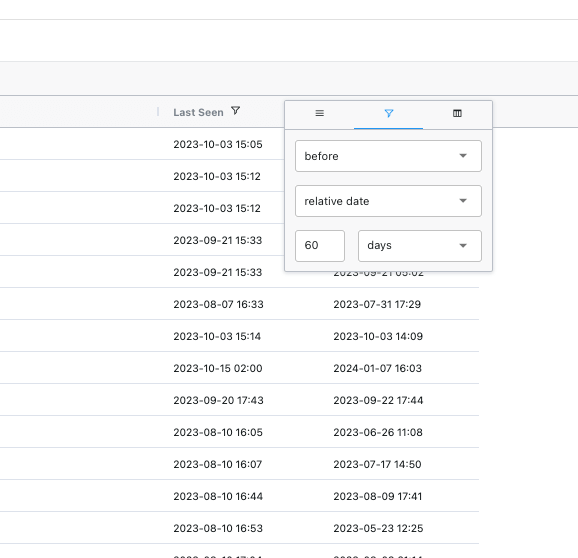
This update enables you to filter your APIs by specific or relative dates. The filter options include “is,” “range,” “before,” and “after,” which allow you to search for APIs in your inventory that meet dynamic date criteria. For example, you can locate APIs that have not been used in the past 60 days or were last modified a week ago. This feature offers greater flexibility in analyzing your API inventory and creating policies that rely on date-based filters.
For additional information about the Noname Security 3.31 release, please review the release notes.