Platform Features
By Need
By Industry
Partner Program
Our Partners
Resource Center
{ "term_id": 176, "name": "Matt Tesauro", "slug": "matt-tesauro", "term_group": 0, "term_taxonomy_id": 176, "taxonomy": "wpx-authors", "description": "", "parent": 0, "count": 6, "filter": "raw" }
How do you secure your organization’s APIs? This is a hot topic and will become even more important as the number of APIs and API traffic continues to grow.
Here are 6 key takeaways on API security.
You are well aware that APIs are a powerful and widely adopted technology integration tool. You know that APIs enable different programs to talk to each other in an efficient, developer-friendly way, even if they weren’t written in the same programming language. In most modern applications, APIs communicate using REST, webhooks, gRPC, or GraphQL.
Historically, organizations had to decide whether to build or buy new technologies. APIs offer a third option: integrating with a partner’s technology applications. As a result, APIs are everywhere in the modern IT world. They are used in cloud migrations, micro services, partner integrations, Kubernetes, DevSecOps, DevOps, and automation.
The volume of API traffic today is already large and will continue to grow. Akamai estimates that in 2019, APIs initiated 83% of global web traffic. Meanwhile, Google Apigee’s data shows that in 2020, API volume increased 49% compared to 2019.
APIs have become the core for modern business.
Two critical elements needed to deliver APIs are:
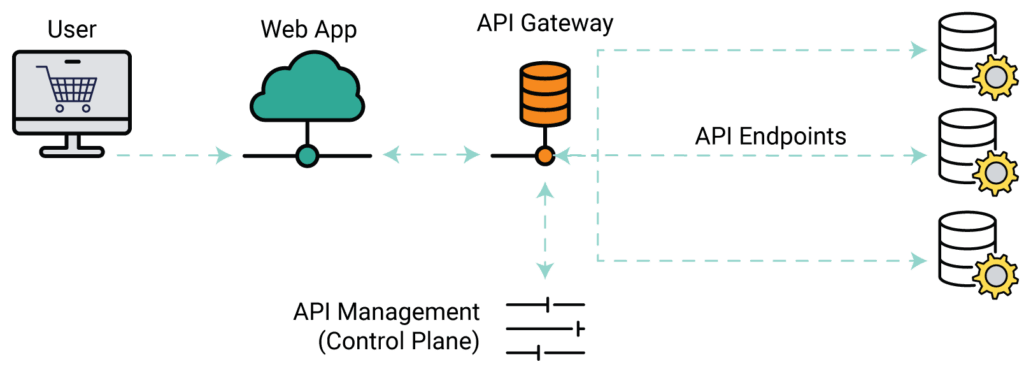
Some security issues related to APIs are similar to those associated with traditional application security, while others are completely different.
Challenges | Solutions |
|
Few businesses have a good handle on their API or application inventory. |
Create an API or application inventory This inventory helps teams identify high-priority security risks. |
|
Security suffers when each app sec team member is responsible for lots of APIs or applications. API sprawl exacerbates this—a single product may be composed of hundreds or thousands of APIs. |
Identify the ratio of staff to APIs or applications Measuring this ratio helps an organization determine if more resources are needed. |
|
App security teams lack good preventive controls to identify problems. |
Deploy the right tools to evaluate security across applications A proactive approach using good tools is far preferable to being reactive. |
|
Many API communication patterns exist. An API may be called by a web app, a command line client, cURL, a continuous integration and continuous development (CI/CD) system, or another API. |
Be prepared to handle diverse API communication patterns Understand all of the various communication patterns that are relevant to your APIs and how to protect them. |
| Test tooling is only starting to mature. Although the Swagger and OpenAPI specifications have made tooling better, it’s still quite weak. |
Deploying robust tooling While it is early days, particularly for dynamic tooling for API testing, tooling is maturing. |
API gateways provide some visibility into security issues, since they serve as a central choke point for protection and policy enforcement. But, not all API calls go through the gateway, making organizations blind to API-to-API calls, as well as to microservice calls that don’t pass through the gateway.
Logging and monitoring usually aren’t very effective. Organizations typically discover authentication threats in APIs only after a breach. In addition, API testing is different from application testing.
To protect APIs, teams must implement several common controls. These include:
Dynamic and static testing are also essential, since the earlier that security vulnerabilities and misconfigurations are caught in the development cycle, the less expensive they are to fix.
Three recommended strategies for API security are:
Understanding the unique challenges associated with API security and having strategies and tools for addressing API security, including automation and continuous testing, can go a long way toward securing APIs.